Aiphone Access Controllers (3)
Browse Access Controllers
- Controller Type
- Networkable
- Standalone
- Standalone/Networkable
- Make
- Aiphone
Access control controller products updated recently
Access control controllers - Expert commentary

In this article, Peter Jackson, Managing Director at Jacksons Fencing, emphasizes the significance of implementing and upholding robust security measures, highlighting their role i...

A study found that over 80% of smartphones have biometric protection enabled, up from 68% a few years ago - these statistics alone show the trajectory of biometric security solutio...

RFID and emerging mobile access technologies are easy to implement and allow elevator access to be integrated with other access control solutions throughout the building, from buil...
Latest Aiphone news

The PSA Network, the world’s largest consortium of professional systems integrators, announced the PSA Partner Program (P3) members for 2024. The P3 program is a perfo...
Aiphone, the international manufacturer of intercom, access control, and emergency communication products, has introduced the AC Nio, its access control management software, an imp...

Organizations of all types have made it a priority to better track who is coming and going inside their facilities and on their property. This can include an HVAC technician who...
Related white papers
Cybersecurity in Keyless Access Management
Three Essential Reasons To Upgrade Your Access Control Technology In 2022
Securing Unmanned Infrastructure at the Network Edge
Mobile access articles
Zenitel, a provider of intelligent communication solutions, announced the launch of two new door entry intercoms: the Turbine Extended Intercoms TEIV1+ and the TEIV4+. The new products display Zenite...
Physical security is essential for a modern production facility, users don’t want just anyone entering the building or accessing secure areas. But what about production machinery? Machine authe...
trinamiX, a provider of biometric solutions, showcases their invisible integration of secure Face Authentication into a foldable screen for smartphones. The solution is integrated behind OLED and off...
Codelocks (Australia) Pty Ltd, an access control company that designs and distributes innovative, standalone keyless door locks, is celebrating ten years of providing leading-edge mechanical and elect...
Gunnebo Entrance Control has reaffirmed its commitment to sustainability, with a bold ambition to achieve net zero emissions by 2045. Grounded in the principles of employee empowerment, ethical busin...
IDEMIA Secure Transactions (IST), a division of IDEMIA Group, is a provider of payment and connectivity solutions for financial institutions, mobile network operators, and automotive manufacturers. B...
Global security manufacturer, Gallagher Security, has announced that support for employee badges in Apple Wallet is available for Gallagher customers in the U.S. with the release of Gallagher Command...
Barracuda Networks, Inc., a trusted partner and major provider of cloud-first security solutions, announced that Neal Bradbury has been elevated to the role of Chief Product Officer. In this new role...
Genetec Inc., a renowned technology provider of unified security, public safety, operations, and business intelligence solutions, announced that its new enterprise-grade SaaS solution, Security Center...
Gallagher Security announced the latest release of their award-winning security site management software, Command Center v9.10, marking a significant evolution for the security platform trusted to pro...
Gunnebo Entrance Control has announced its acquisition of DG Concept and Diadem, a French entrance control, design, installation, and service specialist, marking a significant step in reinforcing its...
Global technology solutions provider - Arrow Electronics, Inc. (ARW) announced that Broadcom selected it as the sole provider for its CloudHealth from VMware offering. CloudHealth is designed to help...
In an industry-first, Safetrust provisions employee and visitor badges directly into Apple Wallet via an email link or text message, eliminating the need to download an application. This innovative a...
HID, a worldwide pioneer in trusted identity solutions, announces the availability of its new HID Seos Essential Bundle, providing small to mid-size businesses (SMBs) in Europe with the benefits of ad...
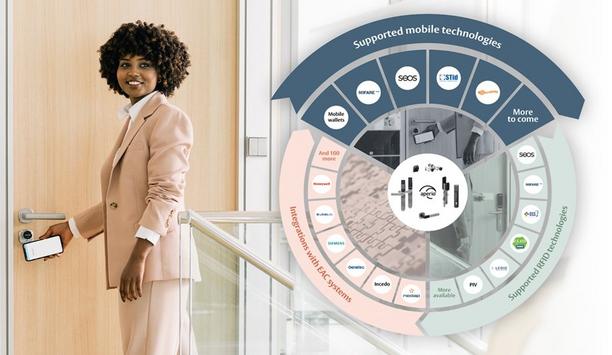
Compatibility with a range of credential technologies can be a critical factor when selecting access control. As organizations across the world explore a move to mobile keys for access, it is more imp...
Healthcare security articles
Milestone Systems, a global pioneer in video technology, is at the forefront of the video security industry, emphasizing responsible technology innovation across its operations. The company will host...
Just like fighting against the spread of disease in a clinical environment, healthcare providers must mobilize, coordinate with interconnected partners, and apply sufficient budgetary resources to com...
Check Point® Software Technologies Ltd., an AI-powered, cloud-delivered cyber security platform provider, has published its Global Threat Index for April 2024. Androxgh0st and LockBit3 atta...
VIPRE Security Group, a global pioneer and award-winning cybersecurity, privacy, and data protection company, released its Q1 2024 Email Threat Trends report, based on an analysis of 1.8 billion email...
Johnson Controls, the global pioneer for smart, healthy, and sustainable buildings, demonstrated complete building security solutions at ISC West 2024 in Las Vegas. The company showcased its comprehen...
Choosing the appropriate fingerprint technology for a given application is dependent on factors including the required level of security and matching accuracy, the desired capabilities and features, a...
ASIS International, the world’s largest association for security management professionals, has announced its programming lineup for Global Security Exchange (GSX) 2024 with in-person and di...
Next DLP, a pioneer in data loss prevention and insider threat solutions announced that their Reveal Platform is the first Insider Risk Management solution to automatically map detection events to MIT...
The Security Executive Council, with Rice University and MD Anderson Cancer Center, will facilitate a day and a half of expert-led sessions on workplace violence risk management for corporate security...
At Hannover Messe 2024, Siemens presents the first generative artificial intelligence (AI) product for engineering in an industrial environment. Siemens Industrial Copilot The Siemens Industrial Cop...
HID, the pioneer in trusted identity solutions, announces it has been positioned by Gartner® as a Pioneer in its 2024 Magic Quadrant for Indoor Location Services. The evaluation was based on speci...
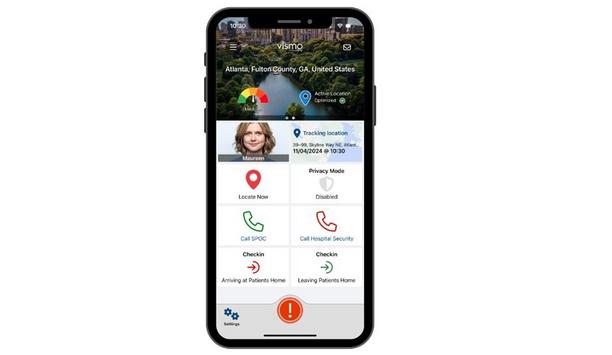
Vismo will launch the latest version of its Locate & Protect App at the International Association for Healthcare Security and Safety (IAHSS) Annual Conference and Exhibition 2024, at booth #713, f...
ASSA ABLOY Opening Solutions will be exhibiting an expanded range of innovative products at booth #8061 during ISC West. With access and intrusion risks rising in schools, healthcare spaces, and worsh...
Cohesity, a pioneer in AI-powered data security and management, announced it is collaborating with Intel to bring Intel’s confidential computing capabilities to the Cohesity Data Cloud. Leverage...
Identiv, Inc., a global digital security and identification pioneer in the Internet of Things (IoT), has entered into a definitive asset purchase agreement to sell its physical security, access card,...
5 Surprising Findings From OT Vulnerability Assessments
DownloadMulti-Residential Access Management And Security
DownloadGuide For HAAS: New Choice Of SMB Security System
DownloadHikvision: Solar Powered Product Introduction + HCP
DownloadFacial Recognition
Download- Madrid Multi-Residential Complex Streamlines Operations With Mobile Digital Access
- Central African Mining Firm Amplifies Efficiency With Matrix's Solutions
- Fashion Label Elevates Security With Matrix's Elevator Access Control
- ExpoFactory Increases Booth Security With ASSA ABLOY's Digital PIN Door Lock Solution