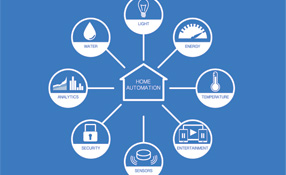
Security and technology are rushing to offer home automation solutions and build out the Smart Home of connected devices and applications. As cameras, alarms, as well as, thermostats and other appliances become controllable and programmable using Internet-enabled smart phones, they are becoming part of a vast web called the internet of things (IoT).
Achieving Greater Value Through Smart Data Exchange
This network of physical objects or "things" embedded with electronics, software, sensors and then connected to the internet holds out the promise to achieve greater value and service by exchanging data with the manufacturer or the installer of a particular device.
“We are all familiar with the internet of people that was created to exchange information between people,” says Alain Louchez, Managing Director of the Center for the Development and Application of Internet-of-Things Technologies (CDAIT) at the Georgia Institute of Technology in Atlanta. “The internet of things is different in the sense we will be integrating into this communication space anything and almost everything. This is the world that is around you, and even things that are inside us with the progress of nanotechnology.”
The appeal of the Smart Home has long been the ability to automate activities such as locking doors and turning systems on and off. Why worry about whether you locked the front door and turned off the stove, when a simple check of your smart phone can reveal their status? And, if you did forget, do the job from afar.
Even through the prices of home automation technology has declined rapidly in recent years, market penetration is only around 10 to 15 percent of U.S. home |
Home owners can also begin to do the kind of data analysis that was once reserved for big companies with large computer networks. They can access reports on energy or water use and for the first time begin to manage in real time how they spend their dollars.
Internet-Enabled Smart Living
As products and devices become connected to the internet, they join others on a two-way street. Just as commands can be sent to them, information about their activities can also be collected and downloaded. This process opens up massive potential for data collection and analysis for not just home owners, but companies as well.
“When we do market research surveys we query people using mail, phone, or personal surveys,” says Louchez. “In the era of the internet of things, why call on people who have limited memory when we can query directly the washing machine or the dish washer to ask them what happened now that we will have all kinds of sensors to get the information?”
A security installer can also check the status of systems they installed. Is there something wrong with the alarm system or the thermostat? Instead of sending a technician out after making an appointment with the home owner, a technician in a distant central station can run the same kind of diagnostics and often correct problems.
That book you viewed on Amazon.com, keeps popping up on your Facebook newsfeed with an insistent nudge to buy. While such monitoring can be creepy, most accept it as just the price you pay for being on a “free” social media platform |
Smart Home Security Risks
There are challenges to achieving widespread smart home adoption. Even through the prices of home automation technology has declined rapidly in recent years, market penetration is only around 10 to 15 percent of U.S. home.
“Certainly, we are already seeing a number of homeowners buying individual wireless products to solve specific home automation needs,” Louchez explains. “However, how these devices work together to offer a true smart home experience is proving to be quite challenging. For example, there are a number of different standards and protocols currently available for smart home technologies, and stakeholders argue that this hinders the smart home’s full potential.”
This easy access to personal data raises questions of privacy and the handling of sometimes sensitive information, according to Louchez.
The appealing convenience of Smart Home devices comes with a sobering downside. They can also send a steady flood of personal data to corporate servers, where it’s stored and even shared with companies and individuals you don’t know and over whom you have no control.
Social Networking Hazards
Users of Facebook and other social media and even smartphone apps have gotten increasingly used to offering their information and activities monitored and accessed. That book you viewed on Amazon.com, keeps popping up on your Facebook newsfeed with an insistent nudge to buy. While such monitoring can be creepy, most accept it as just the price you pay for being on a “free” social media platform.
Earlier this year the revelation that some “smart TVs” might be recording conversations and transmitting them to "third parties" caused an uproar |
Now as connected devices gather personal information from an area long considered private and protected – the bedroom, the kitchen counter, the nursery – the risks are higher than ever. All of the data that various devices and sites have collected can be combined, shifted and then exploited by marketers or even stolen by hackers.
Both manufacturers of smart home products and the companies that install them are feeling pressure to upgrade security standards. They are moving to set policies that will regulate who has access to data and how it is used.
Earlier this year the revelation that some “smart TVs” might be recording conversations and transmitting them to "third parties" caused an uproar. These sets have voice activated features that enable users to change channel, turn on a DVD or browse the internet by speaking to the screen or remote. The fine print in privacy policies contains warnings that general conversations are also being recorded, and one company even told owners to turn off this function if they were concerned.